Gutnov Cyber Arsenal 1.0
Gutnov Cyber Arsenal 1.0
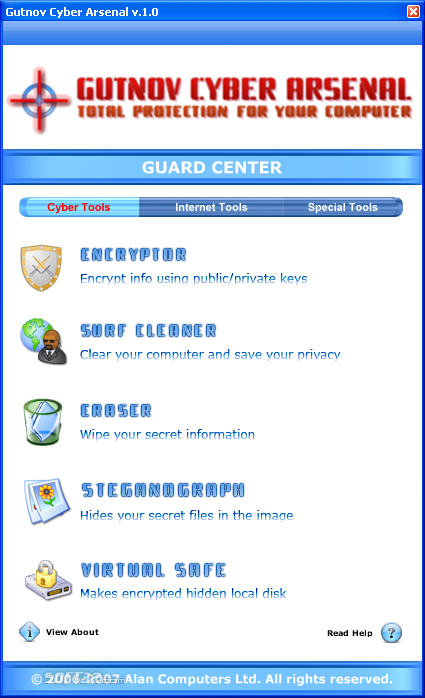
Gutnov Cyber Arsenal ensures the powerfull protection of your personal information and secret files. It lets you encrypt files using asymmetric encryption, shred them, clean internet and computer usage tracks, add secret messages to images, etc.
Last update
4 May. 2007
Licence
Free to try |
$59.95
OS Support
Windows
Downloads
Total: 708 | Last week: 1
Ranking
#666 in
Encryption software
Publisher
Alan Computers Ltd.
Screenshots of Gutnov Cyber Arsenal
Gutnov Cyber Arsenal Publisher's Description
Gutnov Cyber Arsenal is specially developed for the organizations working with confidential data. It also will be useful and to usual users who care of safety of the information. Gutnov Cyber Arsenal protects a computer from not authorized access, provides reliable storage of the information and safe data transmission by e-mail. For storage of the important data the program allows to create a virtual local disk which contents are automatically encrypted after its closing. For encrypting information, are used the most reliable algorithms. Passwords generator will allow you to create the most reliable combination of the password. The special technology protects data from theft. Even knowing the password, the file with data can be opened only on that computer on which it has been created. Another big specialty in program - it is way to hide some secret information by embedding confidential files inside graphic files. It doesn’t alter the actual content or increase the size of the original file – only 2 bytes are added. The built-in system of asymmetric encrypting allows to communicate and send safely the important data by e-mail. The system of destruction of data will provide duly deleting unrecoverable. Quality of deleting of the information corresponds to standards of the Department of Defence of the USA. The special utility will destroy all traces of surfing on the Internet. The set of various network utilities will provide protection against network attacks and trojans, will inform the full information on all network connections, will allow to check up system of safety of the personal computer and to test network. The utility for check of servers will pick up an anonymous proxy-server for safe surfing on the Internet. Gutnov Cyber Arsenal gives set of special tools for creation and storages of passwords, creations of the protected invisible text documents, removals of unnecessary programs, and viewing the information on processes.
Look for Similar Items by Category
Security & Antivirus
> Encryption software
This product is also listed in: Firewall Software, Password Managers
This product is also listed in: Firewall Software, Password Managers
Feedback
- If you need help or have a question, contact us
- Would you like to update this product info?
- Is there any feedback you would like to provide? Click here
Popular Downloads
-
 KaraFun Karaoke Player
2.6.2.0
KaraFun Karaoke Player
2.6.2.0
-
 Kundli
4.5
Kundli
4.5
-
 Macromedia Flash 8
8.0
Macromedia Flash 8
8.0
-
 My Talking Tom
1.0
My Talking Tom
1.0
- FastSum 1.9
-
 FastSum Standard Edition
1.6
FastSum Standard Edition
1.6
-
 Cool Edit Pro
2.1.3097.0
Cool Edit Pro
2.1.3097.0
-
 Cheat Engine
6.8.1
Cheat Engine
6.8.1
-
 Hill Climb Racing
1.0
Hill Climb Racing
1.0
-
 Tom VPN
2.2.8
Tom VPN
2.2.8
-
 Windows XP Service Pack 3
Build...
Windows XP Service Pack 3
Build...
-
 C-Free
5.0
C-Free
5.0
-
 Netcut
2.1.4
Netcut
2.1.4
-
 Vidnoz AI
1.0.0
Vidnoz AI
1.0.0
-
 FormatFactory
4.3
FormatFactory
4.3
-
 Facebook Messenger
440.9.118.0
Facebook Messenger
440.9.118.0
-
 Minecraft
1.10.2
Minecraft
1.10.2
-
 Vector on PC
1.0
Vector on PC
1.0
-
 Horizon
2.9.0.0
Horizon
2.9.0.0
-
 Auto-Tune Evo VST
6.0.9.2
Auto-Tune Evo VST
6.0.9.2